Bringing unmatched cyber HUMINT and investigative expertise to public sector partnerships
Successful operations against cybercrime rely on collaboration and trust — the cornerstones of intelligence sharing between law enforcement and trusted private sector companies.
Intel 471’s Public Sector team is regularly called upon to provide cyber investigation support, threat insights and real-life attribution in support of global law enforcement operations. These partnerships underpin ongoing efforts to disrupt major cybercriminal enterprises, prosecute their operators and deter affiliates.
To nurture these capabilities, we actively recruit and train former law enforcement, intelligence community and military officers from nearly every continent around the world. With over 130 years of collective experience in law enforcement and national security, the Public Sector Team brings unparalleled intelligence, investigations and critical incident support, plus cyber investigative techniques that help our partners reach mission objectives and deliver results.
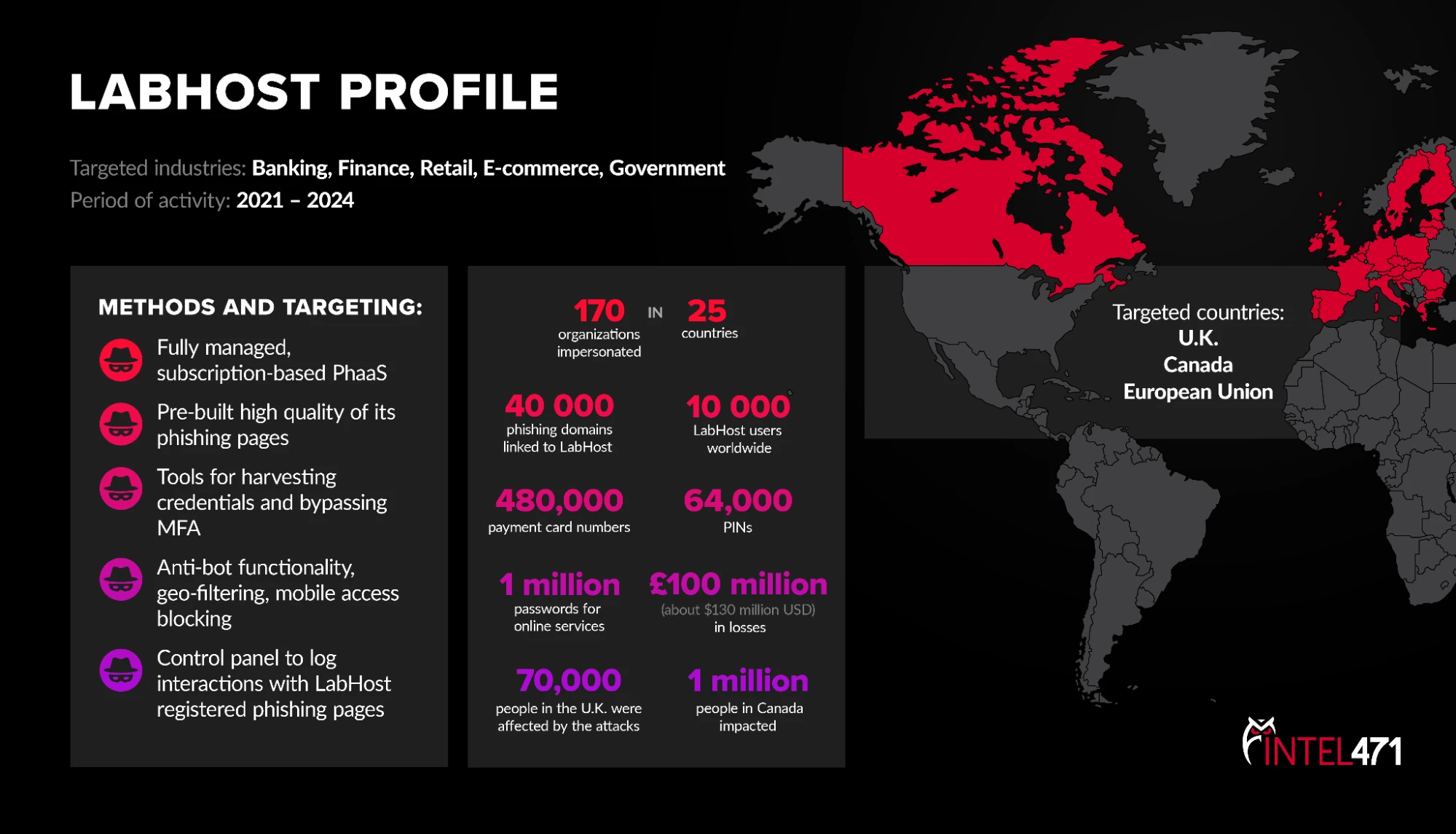
LabHost Phishing-as-a-Service Takedown
In April 2024, law enforcement from 19 countries dismantled one of the world’s largest phishing-as-a-service (PhaaS) platforms, LabHost. The LabHost PhaaS commoditized sophisticated phishing, hosting near-perfect fraudulent pages that impersonated over 170 banks, government agencies, retail brands and online services.
Intel 471 cooperated closely with the UK Metropolitan Police (Met) - London from the early days of their almost two-year investigation dubbed “Operation STARGREW,” which began in June 2022 after the Cyber Defense Alliance shared key intelligence on LabHost’s operations. The Met’s Cyber Crime Unit joined forces with Europol, the UK National Crime Agency, City of London Police, and theUK Regional Organised Crime Units. Partners involved in the takedown included Chainalysis, Intel 471, Microsoft, The Shadowserver Foundation and Trend Micro.
We had been tracking LabHost actors since 2021 and were able to provide the Met a back catalog of forums, shops and Telegram groups that LabHost operators used to sell its products and communicate with buyers. This provided the Met with a deep understanding of LabHost’s history and accelerated its efforts to uncover the identities of the platform’s administrators and top users.
Our contributions included:
- Visibility into the platforms and Telegram channels where LabHost sold its products
- Threat actor communications prior to the investigation
- Investigating LabHost infrastructure and administrators
- Investigating phishing pages associated with users
- Assistance triaging the most active LabHost users
- Assistance with attribution to real-world identities of LabHost admins and its most active users
- Enriching the Met’s investigation with attribution to online handles, email addresses and IP addresses.
The operation resulted in an eight-and-a-half-year imprisonment sentence for one of the UK-based administrators of LabHost. The maximum sentence for offenses under the UK’s Computer Misuse Act is 10 years.
In April 2025, Canadian authorities announced enforcement action against users of LabHost that had defrauded over one million Canadian victims and impersonated over 75 Canadian organizations.
Facilitating Arrest and Extradition through Attribution
Intel 471’s capabilities extend to providing detailed attribution for arrests and extradition proceedings involving some of the most impactful cyber adversaries. Intel 471 has provided support to multiple law enforcement and government agencies for more than a decade, with other publicly acknowledged examples including:
- Following UK sanctions against 16 members of the Russian cybercrime gang ‘Evil Corp,’ the NCA, FBI and Australian Federal Police thanked Intel 471 for its support in a public document outlining Evil Corp’s evolution over the past 20 years, its ties to the Russian state, the launch of Dridex banking malware and recent work as key affiliates of the LockBit ransomware gang.
- Separately, Intel 471 developed real-world attribution of a Ransomware-as-a-Service (RaaS) affiliate who had traveled to Ireland using a fake identity. Intel 471 alerted relevant authorities of the travel and translated online discussions between the suspect and co-conspirators, providing context about their specific role within the RaaS group. The suspect was subsequently arrested and extradited to the U.S. where he has been indicted.
Intel 471 regularly fulfills Requests for Information (RFIs) for custom research to support government and law enforcement efforts to identify and track the physical location of threat actors, as well as translate raw intelligence to help understand threat actor roles, activities and reporting structures.
These and other examples underscore Intel 471’s unique ability to track major cyber threats and apply skilled investigative techniques to enable real-world attribution and decisive law enforcement action. Our dedication to providing rich, near real-time Indicators of Compromise (IOCs) and custom investigations ensures our law enforcement partners gain unmatched intelligence to help protect victims, dismantle criminal operations worldwide and maintain national security.
At the Forefront of Cyber HUMINT
One of the most highly valued differentiators Intel 471 brings to law enforcement and government partnerships is our field-based cyber human intelligence (HUMINT) collection and active cyber counter intelligence. This means engaging threat actors to elicit intelligence, understand how they operate and proactively disrupt their activities. Our approach exploits the need for financially motivated threat actors to operate a business and maintain a presence in the cyber underground. This capability is built around five key concepts used in traditional national counter intelligence for protecting critical infrastructure:
- Identify adversaries who are talking about an organization or its brand using automated collection and direct threat actor engagement
- Deceive adversaries by cultivating personas and creating trusted relationships
- Exploit the behaviors, habits and necessities of financially motivated threat actors
- Disrupt adversary plans before they are fully executed
- Protect assets against adversary intelligence activity
Building and maintaining a cyber HUMINT program is cost-prohibitive, even for governments and large organizations. The high cost comes from mitigating the financial, legal, ethical and reputational risks of operating a cyber HUMINT program in an unpredictable criminal underground environment. These risk mitigation costs result in many organizations providing only ad hoc cyber HUMINT. Doing it at scale with consistency and professionalism requires specialized skills, operational security (OpSec), sophisticated infrastructure and methodologies for collecting and translating unstructured HUMINT into actionable intelligence.
Intel 471 has invested in methodologies, technologies and processes for over a decade to bring these unique end-to-end intelligence capabilities to customers and law enforcement partnerships across the world.
Specialized Skills and Rules of Engagement
Financially motivated and state-sponsored cyber threat actors use multiple identities, personas, and online accounts across various forums and messaging platforms to engage in the criminal underground. Conducting counter intelligence in this environment requires collectors with niche skills, native language capabilities and a knack for jargon to help them move fluidly in the cyber underground, engage with threat actors and maintain access to sources.
Intel 471’s Adversary Intelligence team is skilled at eliciting information from threat actors. They are also trained in and must adhere to strict rules of engagement for conducting active counter intelligence without crossing legal or ethical red lines. Combined with methodical intelligence analysis, these skill sets help partners track individual actors and the evolution of their TTPs, which can help establish links between RaaS groups as they dissolve and rebrand or distinguish activities by interrelated intrusion clusters.
— A UK public sector client
“The information you supplied us about the network intrusion to a UK government site completely aligned with what we have now observed following an incident response investigation, and has assisted in our knowledge of who was likely responsible, thank you.”
— A US public sector client
“Within a few queries I already have an instant connection to the main subject of our case. Really appreciate the training on your tool. Thanks team!”

Our analysts and researchers bring customers a wealth of expertise from previous employment at intelligence, military and law enforcement organizations across the globe.
Methodologies Behind Intel 471’s Intelligence Machine
Our intelligence program is built on multiple frameworks to ensure focus, efficiency, and scale. Our industry-recognized General Intelligence Requirements (GIRs) are part of the methodologies we use to steer collections and deliver a professional cyber counter intelligence program at scale. To achieve this, we apply consistent methodologies and analytic standards, such as NATO's Admiralty System, to translate unstructured human-derived insights into actionable intelligence using cybersecurity frameworks like MITRE ATT&CK, D3FEND, and the National Institute of Standards and Technology (NIST).
The GIR framework helps our analysts and collectors consistently align customer priority intelligence requirements (PIRs) with our cyber HUMINT production, operations and raw data collection. Intel 471’s Collection Management Team (CMT) is the nexus between our intelligence program and customer intelligence teams, ensuring customer PIRs reach collectors in the field, researchers and analysts.
Sophisticated Technology
We’ve also developed proprietary systems to support our malware intelligence work. The Malware Emulation and Tracking System (METS) provides malware emulation, collection and tracking capabilities that enable us to conduct surveillance at the command-and-control (C2) level. The method is akin to gaining a foothold inside of a botnet, which provides real-time visibility of new malicious spam campaigns, new botnet configurations sent by botnet operators and context-rich up-to-date IOCs. This technical data provides invaluable insight to partners, helping drive efficient investigations. The Malware Intelligence team’s finished malware intelligence reports provide deep technical analysis of malware behaviours and the latest TTPs.
Five-Eyes Defense Customer:
“Intel 471 provides us with the single greatest volume of IOC’s out of all 5 vendors. You are the one I advocate and we like the most, as you are the most helpful, most responsive, and when we ask you questions you actually have answers which are clear and make sense.”
A US Commercial Client Involved in Global Incident Response Work:
"The weight and girth of Intel 471's IOC feed is so big that we have had to grow our MISP storage and memory capacity to cope with the volume of your IOC's, it's excellent"
Verity471 — the integrated CTI platform
Verity471, our next-generation cyber intelligence platform, ensures actionable intelligence reaches the right people at the right time. With unique threat insights delivered in near real-time, Verity471 helps customers accelerate investigations and incident response with rich context about threat actor motivations, malware activity and IOCs. Our comprehensive threat intelligence coverage of the cyber underground and regional tension points further strengthen security teams’ ability to identify and prioritize emerging threats. With an integrated library of behaviour-based threat hunting packages, Verity471 also enables proactive hunts for advanced threats that evade detection. Additionally, the platform’s intelligence-driven Cyber Threat Exposure modules help security teams protect their digital attack surface — including third-party and supply chain attack vectors – by identifying and remediating risks before they’re exploited.
Conclusion
The fight against cybercrime is a continuous, collaborative effort that demands trust, expertise and innovation. As cybercriminal tactics evolve, so too must the partnerships and methodologies that underpin effective intelligence and law enforcement operations. Intel 471’s commitment to building world-class cyber HUMINT capabilities, leveraging advanced technology and maintaining close cooperation with global partners ensures we remain at the forefront of cyber threat intelligence.
By providing actionable intelligence, supporting high-impact investigations and enabling real-world attribution, Intel 471 empowers law enforcement and government agencies to disrupt criminal enterprises, protect critical infrastructure and safeguard citizens worldwide. Our dedication to intelligence-driven security and mission-focused partnerships will continue to drive impactful results in the ongoing battle against cybercrime.
