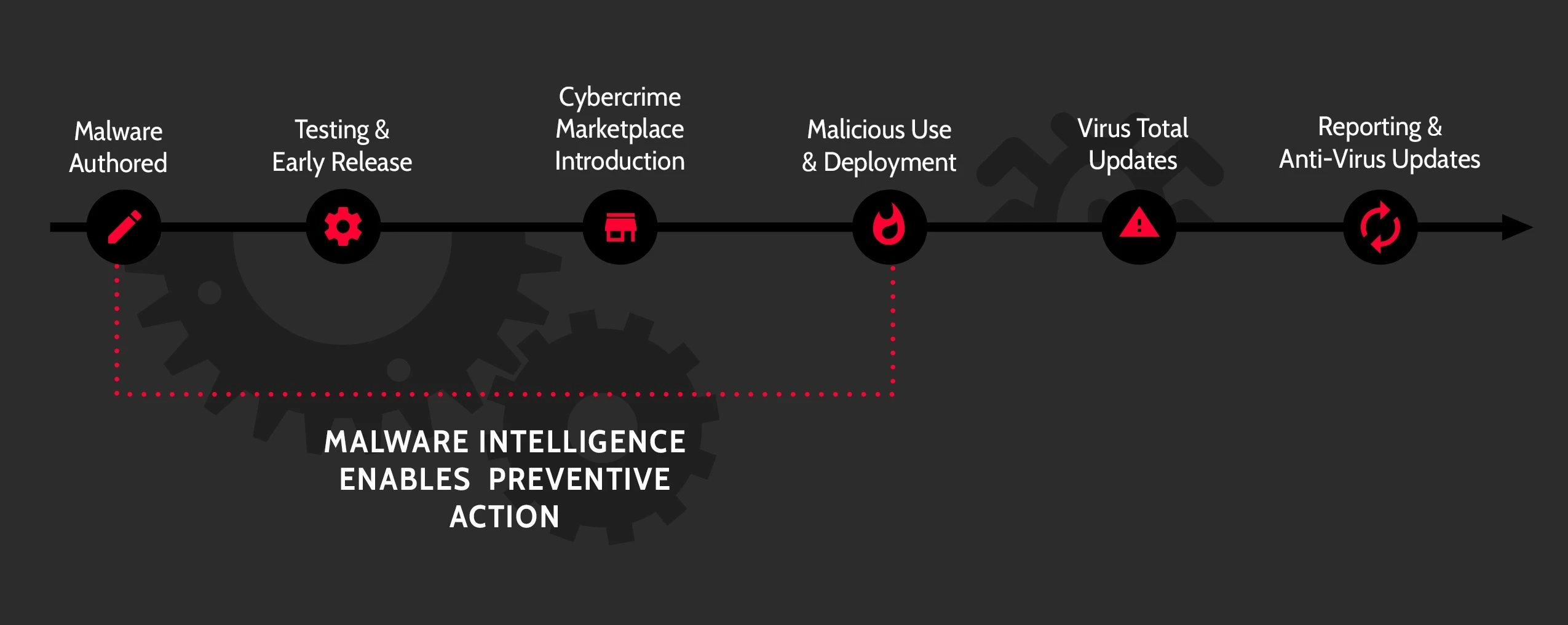
Actively track weaponized and customized threats.

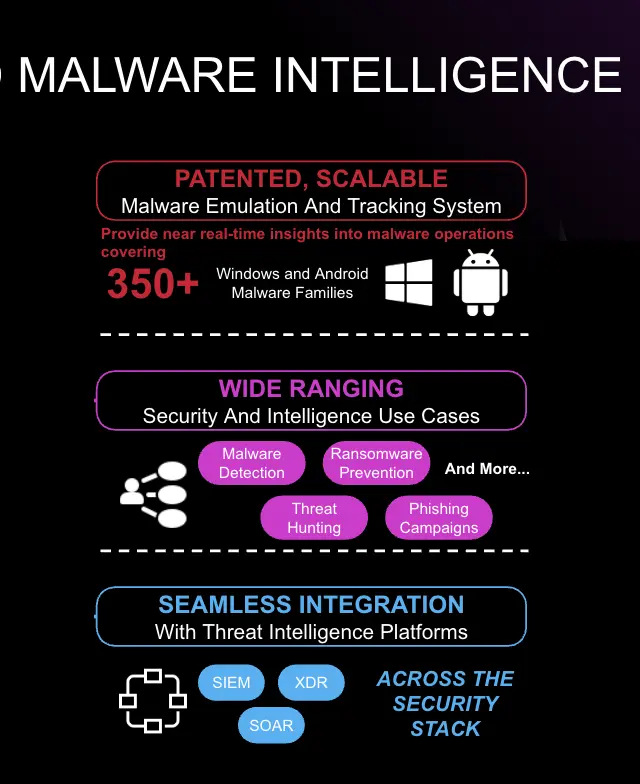
Intel 471’s Malware Intelligence drives a proactive security posture through its continuous monitoring and coverage of malware infrastructure and tools. We provide in-depth coverage across over 285 malware families and over 60 mobile malware families. Track changes to malware, malware campaigns and infrastructure updates to neutralize threats targeting your organization.
Malware Intelligence provides near-real time proactive insights into malware and related threat actor activity using the Technical Research & Analysis Platform (TRAP), our automated framework for tracking and monitoring malware.
TRAP is further enhanced with near-real time surveillance of malware activity at the command-and-control (C2) level, providing deep insights and context into malware operations using our unique and patented Malware Emulation and Tracking System (METS). METS delivers near real-time insights and deep context in support of numerous cybersecurity and intelligence use cases.
Coverage of top-tier malware families
Coverage of loaders, information stealers, banking malware and ransomware
High-fidelity data with low or no false positives
Near real-time malware surveillance data via METS
Track campaigns, C2 infrastructure and malware updates
Creates efficiencies on cycles required to track malware
Access YARA rules, Spot Reports, in-depth technical reports, actor links, raw data and indicators of compromise
Malware Intelligence Reports providing analysis of malware families and features, network traffic, how to identify, detect and decode it, extract and parse its configuration, control server(s) encryption key and campaign ID.
In-depth Tactics, Techniques, Procedures and Context to enable a detailed understanding when events are detected and blocked. This includes, but is not limited to, linked malware family and version, encryption key, botnet ID, plugins used, expiration time and associated intelligence requirements.
Timely and high-fidelity File and Network Based Indicator feeds that can be automatically ingested and operationalized within security stacks to block and detect malicious activity from malware.
YARA Rules and IDS Signatures to accurately identify and detect malware families, malicious network traffic and improve detection systems.
Malware and Botnet Configuration Information providing decoded, decrypted and/or parsed configuration information enabling insight on specific targets of banking trojans, spam campaigns or other secondary malware payloads.
Monitoring of Command and Control (C2) servers to capture commands and updates initiated by threat actors to include secondary payloads, plugins, modules and anything delivered to the bot from the adversary. All data is available for download for local processing and analysis.
Video: Learn how you can stay a step ahead of this threat activity.
Mobile Malware, a key feature of our Malware Intelligence offering, tracks the top-tier families focused on systems access, information stealing and financial fraud to allow you to detect and prevent account takeover, two factor authentication (2FA) bypass, fraud and data leakage from employees or customers.
Build a comprehensive picture of the Android malware landscape by combining in-depth analysis and tracking of mobile malware families and instances with tracking of the actors behind the development, sale and use of mobile malware across the underground.
Stay informed with our weekly executive update, sending you the latest news and timely data on the threats, risks, and regulations affecting your organization.