Today, cyber attacks are frequently coordinated, sophisticated, and targeted. Geopolitics has complicated the threat landscape as nation-state and cybercriminal actors converge upon shared infrastructure and the abuse of trusted administrator tools to evade detection and further their objectives in data extortion, fraud, or espionage. The rise of software-as-service (SaaS) has also made employee identity data a prized target for cybercriminals, driving new phishing techniques and an underground economy in stolen credentials, information-stealing malware, and third-party breaches.
Security teams overwhelmed by data too often miss time-sensitive cyber threat intelligence (CTI), leaving them on the back foot. However, defenders can turn the tables with a proactive cybersecurity strategy that infuses actionable CTI into every aspect of their security program across threat hunting, detection, response, and remediation.
To shatter the cycle of reactive defense, Intel 471 is launching Verity471, the evolution of our trusted cyber intelligence platform, TITAN. Our next-gen platform gives your security teams the intelligence advantage, helping them know their attack surface better than adversaries, hunt down advanced threats that beat the best detections, and prioritize exposures that matter most to them.
Meet Verity471, the evolution of TITAN
For over a decade, TITAN has served some of the world’s most mature CTI programs, playing a critical role in their proactive cybersecurity strategies and operations against cybercrime. TITAN is also the primary platform our intelligence analysts use to curate, structure, and disseminate the insights we gather on top-tier threat actors, malware, breaches, vulnerabilities, compromised credentials, and marketplaces for cybercriminal products and services. It is the conduit to the unique insights we gain through direct actor engagement and surface with expert analysis of their motivations, tools, and behaviors.
Today, there is pressure on CTI teams to meet diverse business needs as boards and business leaders exert more influence on intelligence priorities to reduce business risk, secure supply chains, reduce third-party risk, and strengthen operational resilience. This shift is happening amid heightened geopolitical tensions that have given rise to cyberwar, destructive cyber attacks, and hacktivists targeting critical infrastructure.
Verity471 is built to meet these challenges by giving teams a single platform to amplify the operational readiness of CTI for intelligence-driven prioritization, threat hunting, threat exposure detection, response, and remediation. The platform, fuelled by Intel 471’s human intelligence (HUMINT) expertise, can help teams apply threat intelligence across all security and business challenges to efficiently reduce risk and drive resilience.
Three Portfolios in One Platform
With Verity471, security teams can seamlessly pivot between Intel 471’s three portfolios — Cyber Threat Exposure, Cyber Threat Intelligence, and Cyber Threat Hunt — to access our expert analysis and reporting, tools, and dashboards from a single, intuitive platform. This unified CTI-powered platform is designed to provide intelligence that’s ready to operationalize out of the box.
To achieve this goal, Verity471 introduces Intelligence, Exposure, and Hunt modes on a unified CTI-powered platform that ensures security teams never miss an opportunity to operationalize our premier adversary intelligence, whether they’re hunting undetected threats, remediating high-risk attack surface exposures, identifying visibility gaps in security configurations and network architecture, or staying ahead of the most prolific malware and adversary tactics, techniques, and procedures.
Verity471’s Mode Switcher serves as a single point of access to reach all Intel 471 portfolios without needing to reauthenticate, delivering an intuitive experience that accelerates workflows across threat hunting, threat research, and analysis.
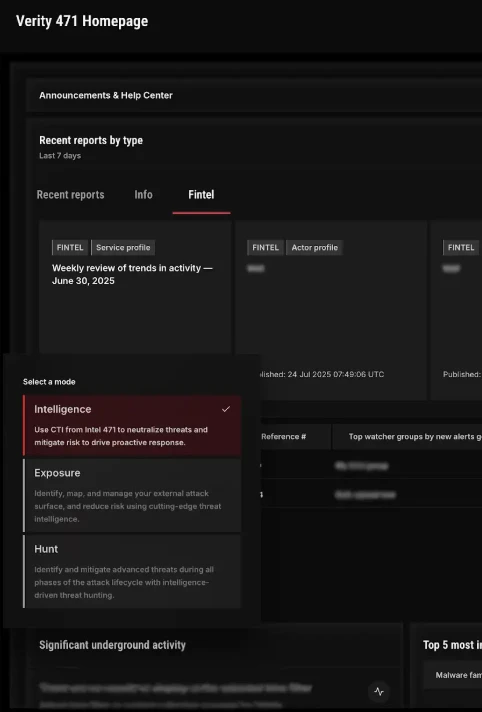
Introducing Exposure mode — Closing the CTI capability gap
Not all security teams enjoy support from mature in-house CTI programs; and even the most capable CTI teams require swift actionability of tactical intelligence data so they can spend precious resources on more sophisticated threats. Exposure mode on Verity471 addresses this CTI capability gap by putting Intel 471’s premier adversary intelligence and continuous CTI data collection from the cyber underground in the hands of all security and risk teams, enabling CTI programs at all levels of maturity to quickly detect and address external threats that matter most to their organization.
The first modules of Verity471 Exposure mode are Attack Surface Exposure, which identifies exposures affecting an organization’s own attack surface; and Third-Party Exposure to monitor and mitigate risk from exposures affecting critical third parties. Both modules map our CTI to exposures, enabling teams to prioritize remediation efforts to high-risk exposures and proactively mitigate risk from third parties. The modules also help mature CTI teams meet the mounting pressure to do more with less. Thoughtfully designed dashboards surface critical findings to help overstretched teams quickly understand risk and easily pivot to relevant CTI context to prioritize remediation.
Read more about how Attack Surface Exposure and Third-Party Exposure modules can help your organization at our blogpost Bridging the CTI Gap: New Exposure Modules on Verity471.
Hunt mode — Never miss a beat on evolving TTPs
With Verity471, we’re fusing our on-the-ground adversary intelligence, expert analyses of emerging TTPs, and patented malware emulation and tracking system with our world class behavioral threat hunting capabilities.
Hunt mode on Verity471 provides full access to HUNTER, Intel 471’s growing library of behavioral hunt packages, which your teams can immediately execute on your security platforms to identify undetected threats. We believe our intelligence-driven hunt packages, fuelled by our unique adversary and malware insights, are the most powerful form of intelligence to counter threats that use advanced behaviors and techniques - including leveraging Living off The Land tactics and binaries (LOLbins) - to evade detection. HUNTER packages are also the most direct way security teams can operationalize CTI on their security platforms to neutralize advanced threats.
Hunt mode provides fully formed hunt content. Our team does the heavy-lifting work of research and hypothesis testing, hunt query writing, and validation for most advanced TTPs solving the challenge of stale or ineffective hunt content caused by resource constraints that hold back research and new query logic development. Each hunt package is continually updated with CTI context and tagged with MITRE ATT&CK technique IDs, threat names, categories, industry, geography, severity, motivations, and related exploits and vulnerabilities. This gives hunters the context they need for effective prioritization and campaign building.
Your threat hunters can easily pivot between Hunt mode and Intelligence mode to dive deeper into context that matters, investigate threat actor and cybercriminal service profiles, and view real-time updates across our intelligence domains. This powerful capability for intelligence-driven threat hunting expedites research, enabling advanced hunt teams to build new hunt content for threats specific to their sector or organization.
Equally important, Hunt mode provides the hunt content and tools to build successful human-led in-house threat hunting capabilities and overcome the ongoing shortage of seasoned threat hunters (https://intel471.com/blog/six-key-takeaways-from-the-sans-2025-threat-hunting-survey). To learn how, see our paper on findings from the SANS Institute’s 2025 Threat Hunting Survey.
Hunt Management Module — Consistent metrics and expert Guided Threat Hunts
Our industry-leading Hunt Management Module on Verity471 helps threat hunting teams scale up productivity with consistent and repeatable hunts. Hunt teams use the module to operationalize hunts, track progress, manage findings, and report on team effectiveness. The module addresses the need for consistent methods of tracking hunt statistics and metrics that demonstrate hunt effectiveness, a common shortcoming in hunt programs that results in siloed efforts and unclear return on investment.
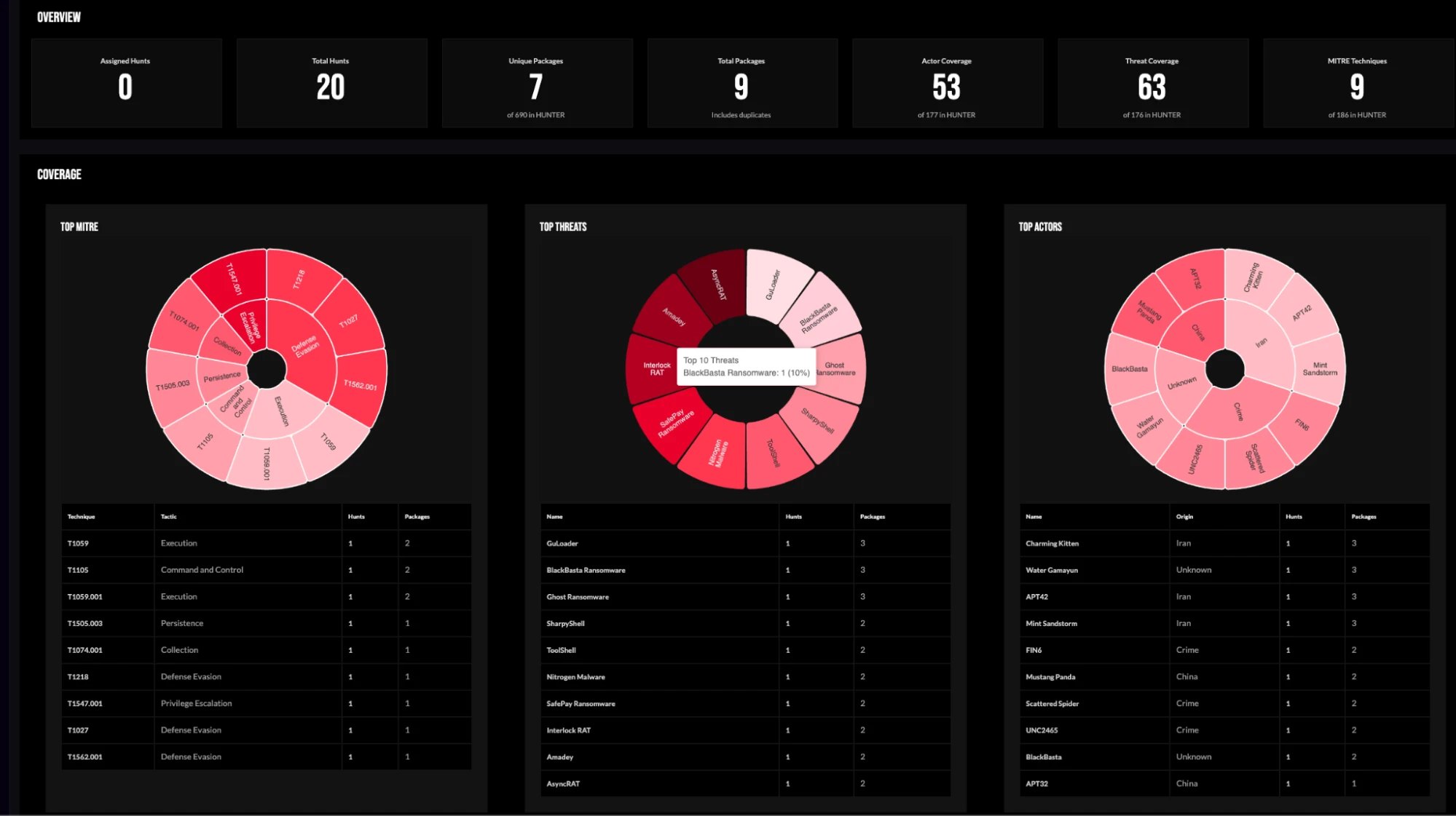
Hunt Management Module dashboard provides visual representation of organization's actor, threat, and MITRE TTP coverage
Guided Threat Hunts — unique in the industry
Guided Threat Hunts, a new feature of the Hunt Management Module, helps your team hunt for threat indicators with greater speed, decisiveness, and consistency.
Running an initial query on a security or data aggregation platform can return large results. Guided Threat Hunts provides assistance to craft follow-on queries to efficiently investigate notable artifacts. It also provides filters to exclude noise and narrow large data sets. Unique in the industry, Guided Threat Hunts offer a library of Pivot Queries for hundreds of our hunt packages that help your team overcome uncertainty, boost productivity, and drive standard operating procedures to support their hunt methodology.
Bring Your Own Hunt (BYOH) packages
Many advanced threat hunting teams have a wealth of organization- or sector-specific hunt packages. With BYOH, organizations can maximize the value of hunt content their own team builds. This feature of the Hunt Management Module allows hunt teams to bring their existing hunt queries to HUNTER and develop new custom hunt content aligned with our industry-leading methodology for hunt creation and management. It instills consistent practices for hunt documentation and CTI contextualization to improve hunter efficiency, collaboration, and hunt decision making.
Intelligence mode - Finding and acting upon new and unique adversary and malware intelligence first
The Verity471 Intelligence mode builds on TITAN’s strengths for intelligence production and dissemination with powerful search, dashboards, tabs, and a new AI Assistant that are designed to help analysts achieve their mission of finding and acting upon new and unique adversary and malware intelligence first — whether they’re combatting fraud, mitigating a ransomware attack, or profiling and hunting advanced threats. Verity471 Intelligence mode is a critical tool for teams operationalizing our premier CTI for malware and campaign detection, incident response, monitoring compromised credentials, dark web monitoring and investigations, account takeover protection, and prioritized patching of high-risk and weaponized vulnerabilities.
Homepage Dashboard
The new homepage dashboard on Intelligence Mode surfaces the most critical and recent threat information from across Intel 471’s intelligence domains, enabling CTI teams to deliver actionable and timely TLP: AMBER+STRICT insights to their security and risk stakeholders in their organization. The dashboard is the natural starting point for CTI analysts, detection engineers, vulnerability analysts, fraud teams, and threat hunters investigating top-tier threats and their evolving TTPs.
The homepage dashboard provides quick access to our latest intelligence reports curated by our industry-leading experts around the world including spot reports, finished intelligence (FINTEL) reports, adversary profiles, breach alerts, and more. It also provides a snapshot of the most impactful malware families and an entry point to our patented malware emulation and tracking system’s deep insights into the command-and-control infrastructure used by infostealers, remote access trojans, banking malware, and downloaders for distributing ransomware and other payloads. Users can survey the top new vulnerabilities in our Vulnerability Intelligence Dashboard and drill down to risk details for prioritization, such as the exploit status of the CVE and associated underground activity, and pivot to related FINTEL reports for deeper research and context surrounding a CVE’s exploitation.
Powerful Search and Filters
Verity471’s powerful search helps threat hunters and analysts research using precise queries, with new auto-suggestion fields that appear while typing queries, and Custom Range search for time-bound investigations. The main left-side menu enables easy pivoting to raw CTI data from the Sources view to gain real-time insights into threat actor communications, breach claims, and product offers across dark web forums, messaging channels, and data extortion leak sites. Users can filter results by date, datasets (e.g. Reports, Forums, Messaging services, etc.), and by Intel 471’s industry-recognized General Intelligence Requirements (GIRs), such as illicit forums, instant messaging channels, marketplaces, products, services, and adversaries.
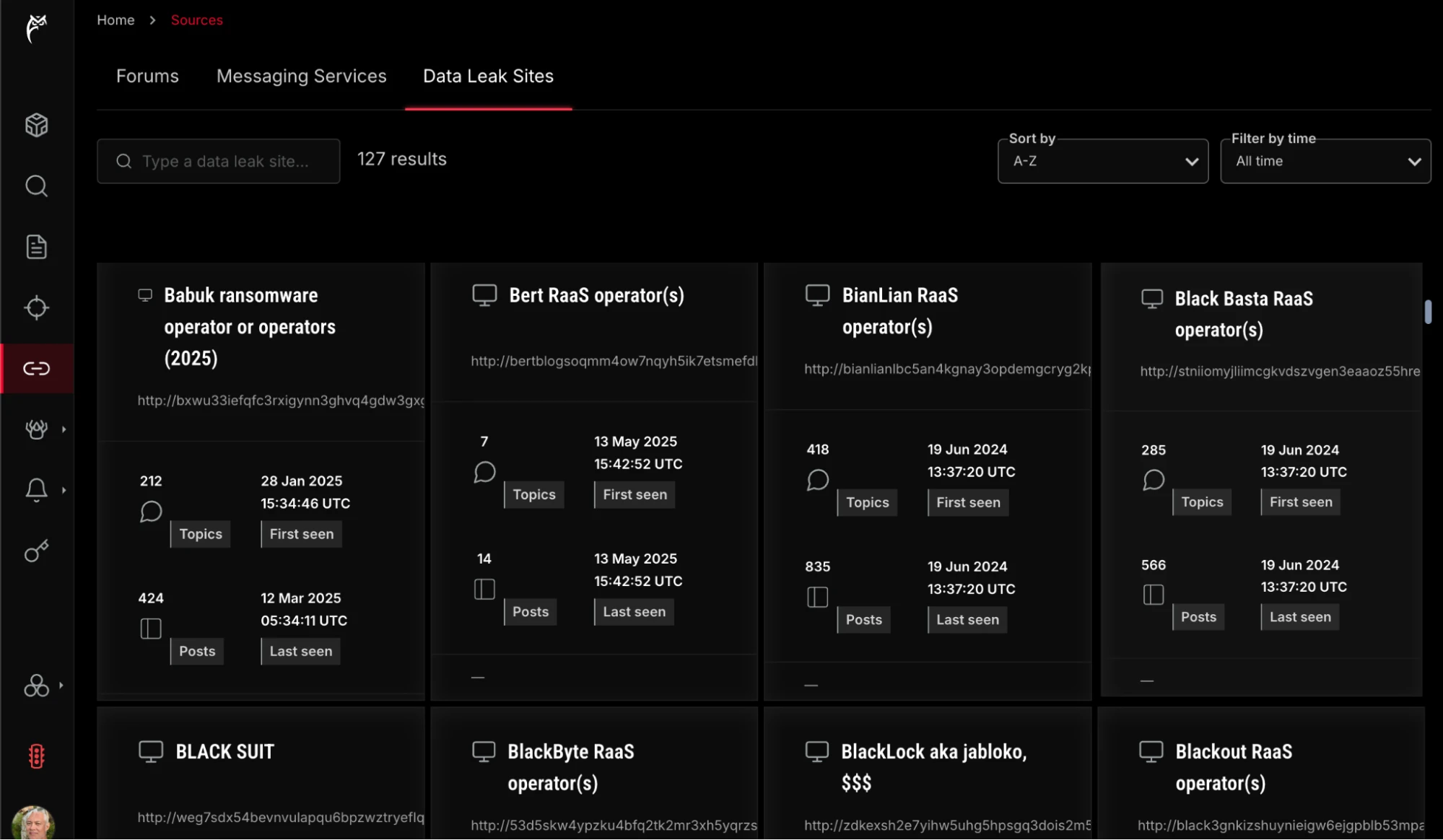
Monitor Ransomware-as-a-Service breach claims and leaks.
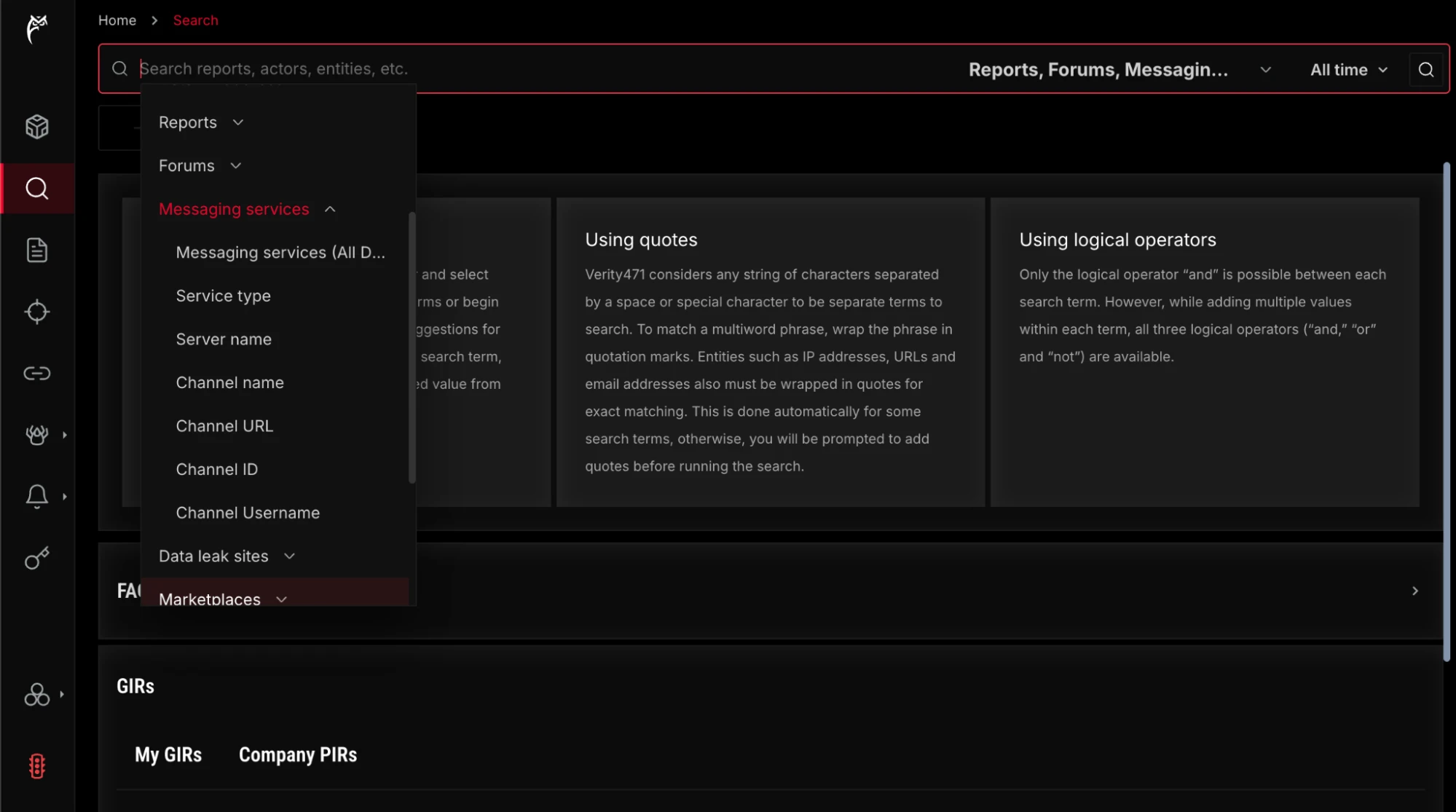
Verity471’s powerful Search enables refined queries and filtering data sources
Curated Dashboards for Vulnerabilities, Malware, and Credentials
Users can pivot to the dynamic Vulnerabilities Dashboard, Malware Dashboard, and Credentials Dashboard for a quick overview of threats to your organization. The Credentials Dashboard now contains richer metadata extracted from infostealer logs that provide deeper insights into how these credentials were compromised. The Malware Dashboard’s activity graph for each malware family provides a visual representation of its trends and prevalence over time, and links to Malware Profiles that show an overview of the malware, version history, YARA detection signatures, detailed malware reports, and significant events. The Vulnerability Intelligence Dashboard features a drawer for each CVE that slides out after clicking on the CVE and exposes a wealth of risk information without having to navigate away from the main table.
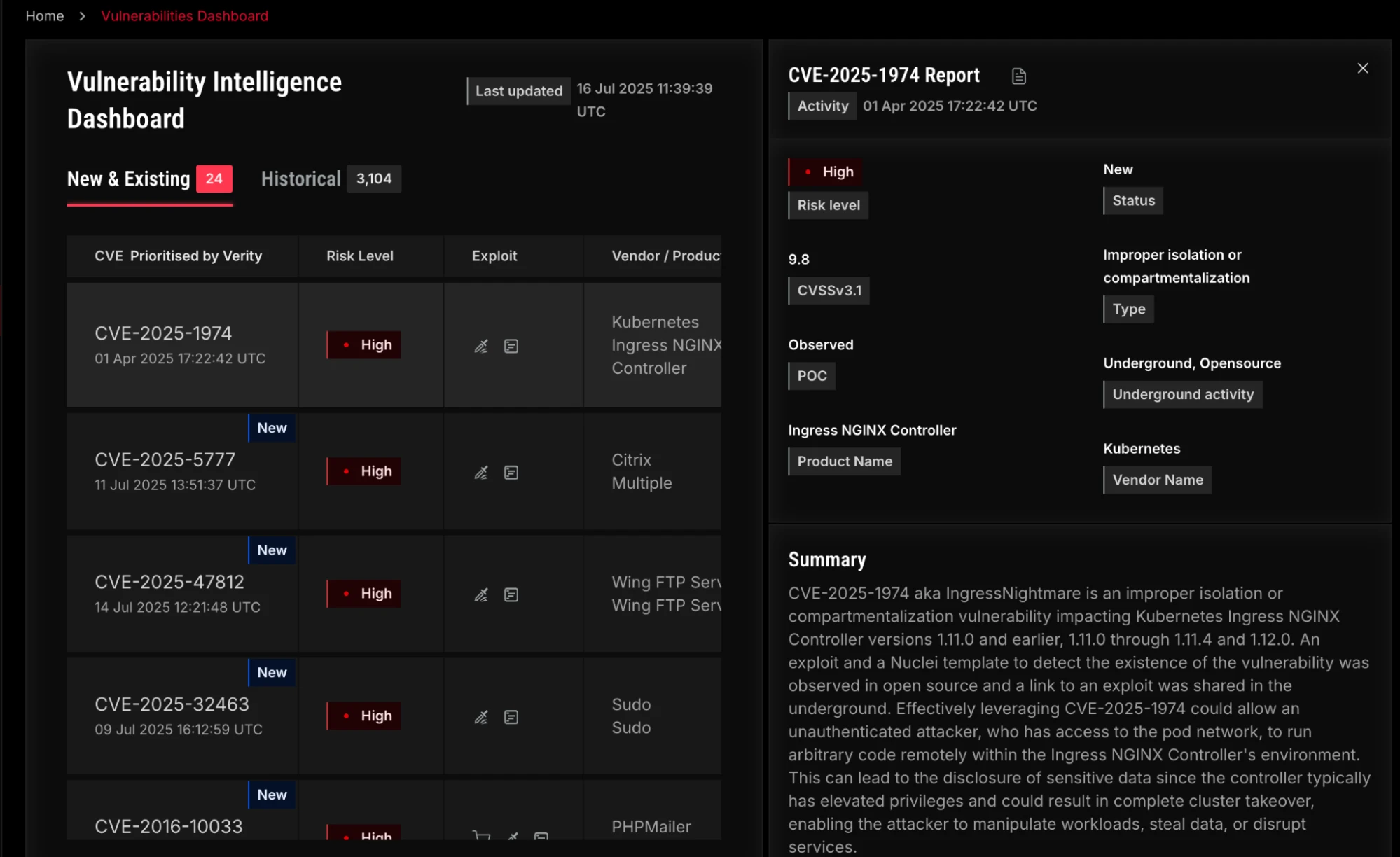
Vulnerability Intelligence Dashboard slide-out drawer
AI Assistant
The new AI Assistant in Intelligence Mode empowers users to get more out of Intel 471’s comprehensive picture of the external threat landscape. Powered by one of the top ranking large language models (LLMs), the AI Assistant excels in summarization, data extraction, formatting, cross-report correlation, and tailoring content for different audience needs across tactical, operational, and strategic intelligence reporting.
Users can, for example, ask the AI Assistant, Why is this report important?, and prompt it to create a report for the Security Operations Center (SOC) summarizing indicators required for detection and add a table with the corresponding TTPs and MITRE ATT&CK technique identifiers.
We prioritized data integrity and data privacy when designing our AI Assistant by, respectively, restricting external data sources and ensuring that none of our data is used to train the underlying AI model. We’re taking a thoughtful approach to AI, ensuring that AI enhances efficiency and minimizes the chance of inaccurate insights into complex adversary behaviors. In the coming months, we’ll be expanding our data sources from reports to include forums and messages, and will enhance our global search function to provide AI-powered summaries of any search query and support natural language search terms.
Marketplaces
Marketplaces on Verity471 offers a window into Intel 471’s comprehensive automated collection from underground marketplaces, spanning a broad array product categories including Payment cards, Stealer malware logs, Exploits, Illicit Drugs, Digital goods, Database dumps, PayPal accounts, Personally Identifiable Information (PII), Forged documents and scans, Stolen accounts, Stolen bank accounts, and Proxy Servers.
The Marketplaces module was designed based on our users' search and navigation patterns. This approach resulted in a more structured and improved experience, helping users quickly find relevant information. Users gain visibility into key marketplace details, including vendor names, full-text listing descriptions, product volume by category, and marketplace activity graphs. Individual marketplace pages offer Vendors and Products tabs, providing a side-by-side view of listings with detailed product summaries. An “Explore Product” button allows users to navigate to and share product information.
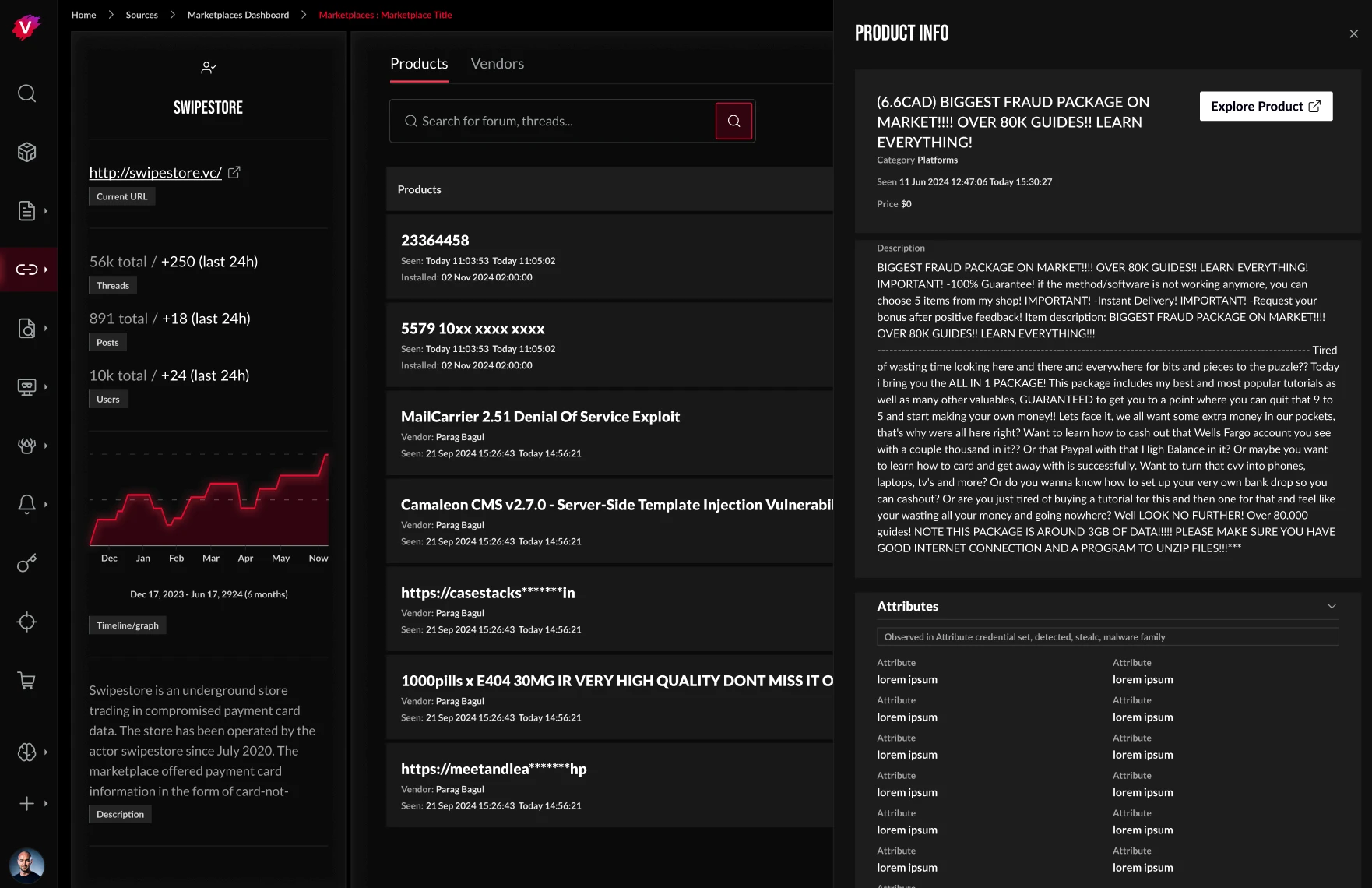
Marketplaces shop view offers
Watchers and Advanced Features
The Watcher and Alerts module is an efficient way to monitor new and relevant information as it comes in. Users can set up and fine tune Watchers to automatically alert them whenever new intelligence matching their criteria is added to Verity471. A key aspect of watchers is collaboration. Users can share Watcher alerts with team members, ensuring everyone is on the same page. Team members can also assign statuses to alerts, allowing for clear tracking of investigation progress and ownership within your team.
Verity471’s advanced features allow users to create bulk watchers by directly uploading a list of Organization Specific Intelligence Requirements (OSIRs) using CSV files populated with, for example, domains, brands, suppliers, email addresses, IP addresses. Users can select the OSIR Type (e.g. ASN, ActorHandle, BIN, Brands, CVE, Domain, EmailAddress, GCBIN, Goods, IBAN) and then execute a search using your uploaded OSIRs. After uploading the file, users can run a search against any or all datasets and combine the list with other parameters to narrow results. Users can monitor organizational specific data using the Verity471 Watcher and Alerts module and use Intel 471’s industry-recognized General Intelligence Requirements (GIRs) to help with search and filtering.
See Verity471 in action today
Verity471 is designed to support the strengths of different cybersecurity and security operations teams, helping them counter advanced threats with intelligence and tools to operationalize CTI for detection, response and remediation with behavioral threat hunts that establish consistent proactive defense. By applying threat intelligence to not just security but business challenges, teams can efficiently reduce risk and improve operational resilience.
To see how Verity471 can improve your proactive cybersecurity strategy, download our new white paper The Black Basta Blueprint: Your window to the ransomware group’s inner workings. The analysis of Black Basta’s behavior equips organizations with the insight needed to defend against these actors as they resurface under different guises in the future. It also demonstrates how Verity471 helps your teams transform insights into action. With fully contextualized intelligence on the Black Basta leak from the attackers’ perspective, our security experts, intelligence analysts, and threat hunters provide a useful guide to using our portfolios across Threat Exposure, Threat Intelligence, and Threat Hunting to transform intelligence into action. And if you’re attending Black Hat 2025, come by our booth #5742 to get a live demo of Verity471 or book a meeting with an Intel 471 Pro here: https://intel471.com/lp/black-hat-usa-2025
