Introduction
A new threat actor has launched what appears to be a fake ransomware-as-a-service (RaaS) operation called 0APT. Over the last week, 0APT published a data leak site (DLS) with fake companies. However, the actor has caused alarm in the past few days after publishing the names of several real organizations and has reportedly prompted some companies to initiate incident response processes.
Investigation
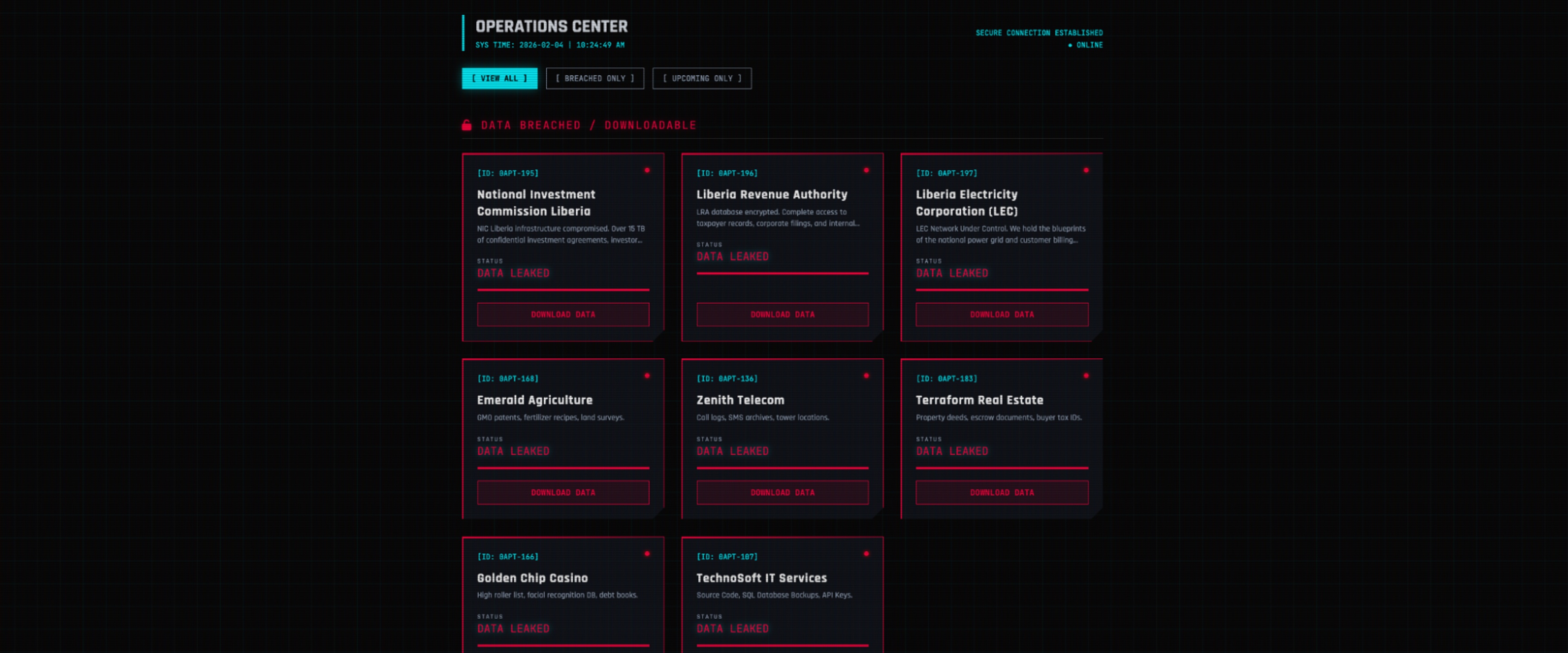
The threat actor 0APT appeared in January 2026 and within only a few days claimed more than 150 victims via its DLS on a Tor-based domain. However, it quickly became clear that many of the alleged victims could not be verified and appeared to be artificially generated.
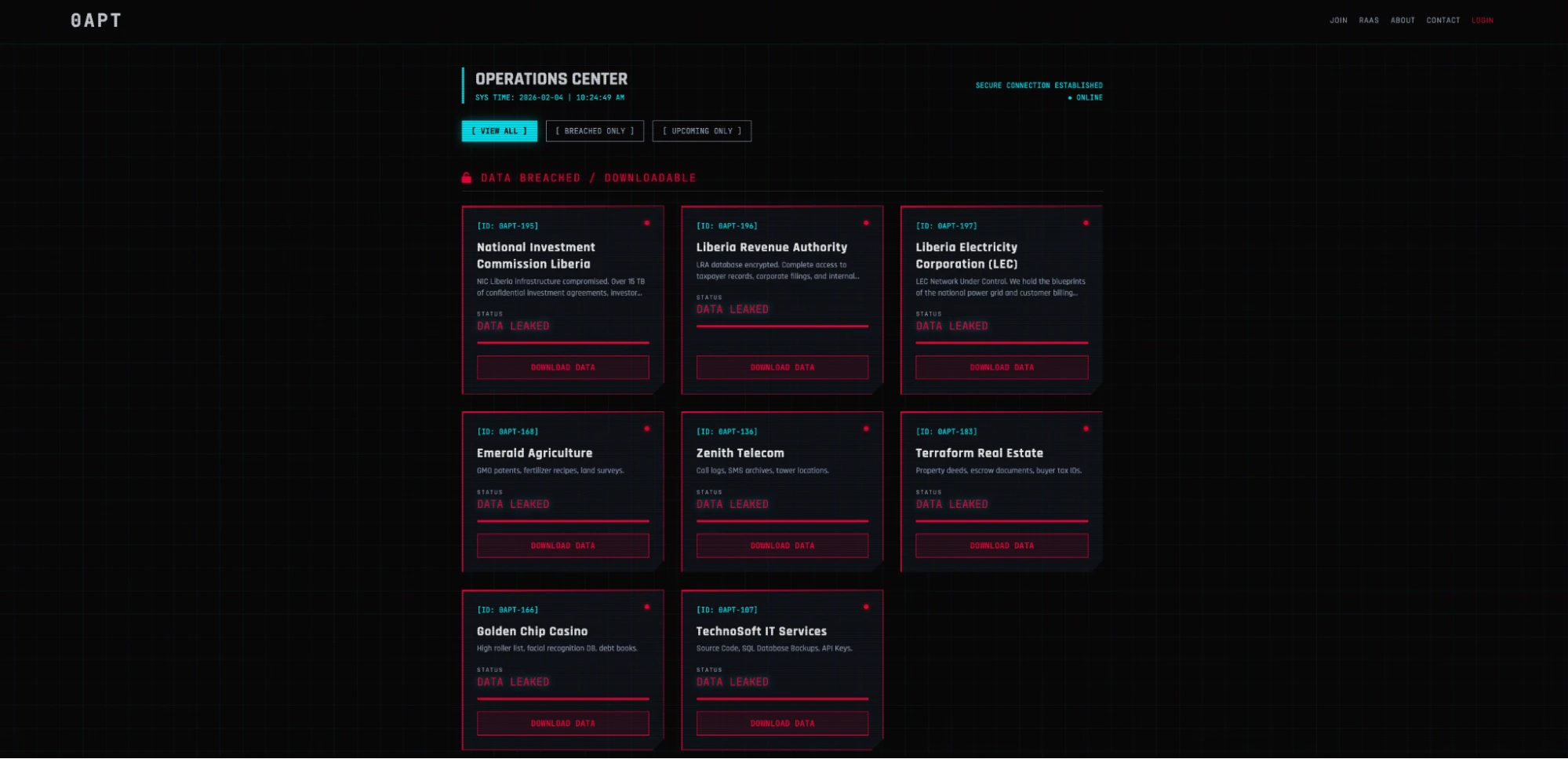
The image depicts a screenshot of the main page of the 0APT DLS Feb. 3, 2026.
Thus far, the threat actor has not provided credible proof of ransomware or data exfiltration attacks as the data samples on the DLS appeared to be fabricated. As the string of alleged victims was revealed, Intel 471 researchers conducted a preliminary review of the DLS metadata and content and found numerous abnormalities. For example, the files that supposedly contained metadata of data stolen from victim networks was unusually large, reaching several terabytes each. Additionally, partial downloads of those files indicated they did not contain any useful data and in fact we observed several instances in which the content contained a repeating pattern of null bytes.
The sheer number of victims listed in such a short time was also highly suspicious, albeit not unprecedented. For instance, Intel 471 reported the Qilin RaaS program was the most impactful in January 2026 with over 100 claimed breaches.. Additionally, in 2023, the CLOP group exploited vulnerabilities in managed file transfer (MFT) servers and claimed as many as 130 victims. However, unlike 0APT, CLOP is a proven and persistent threat group with an established reputation.
To round off the team’s analysis, Intel 471 discovered the alleged 0APT malware sample. As detailed in our internal customer-facing reporting, technical analysis of the malicious file indicated it was more of a work in progress than a fully operational ransomware malware sample.
Conclusion
Ultimately, our threat analysts’ assessment led us to report that 0APT made doubtful claims about breaching more than 150 companies worldwide. However, there is a small possibility the actor was simply testing capabilities and infrastructure for future planned activity. Therefore, and out of an abundance of caution, the Intel 471 Threat Hunt team worked with Malware Intelligence analysts to identify applicable threat hunt packages associated with 0APT’s activities, which are available for Intel 471 Threat Hunt module subscribers.
- Winrar Archive Created
- Remote WMI Command Attempt
- Network SMB Profiling - Potential Nonstandard SMB Communication Behavior
- Remote Services - SMB Share mounts/admin shares/scanning
- Shadow Copies Deletion Using Operating Systems Utilities
- Attempt To Set Default PowerShell Execution Policy To Unrestricted
- Methods for Downloading Files with PowerShell
- Excessive Windows Discovery CommandLine Arguments - Potential Malware Installation
Defender guidance
1. Validate breach claims before escalationWhen a new or unknown ransomware group claims to have compromised your organization, do not immediately assume the claim is legitimate. Carefully review the evidence provided on leak sites or in extortion communications. Look for credible proof of data exfiltration, such as unique file samples, internal documents or data that could only have been obtained from your environment. If the data appears generic, corrupted or artificially generated — as in the case of 0APT — treat the claim with skepticism and conduct a thorough internal investigation before triggering a full-scale incident response.
2. Monitor for associated malware and TTPsEven if the extortion claims are dubious, remain vigilant for any malware or tools associated with the actor. Defenders should monitor for behaviors such as suspicious PowerShell activity, creation of WinRAR archives, remote Windows Management Instrumentation (WMI) commands, nonstandard server message block (SMB) communication, shadow copy deletion and attempts to set PowerShell execution policy to unrestricted. These are indicative of post-exploitation or lateral movement attempts.
3. Tune security operations to reduce alert fatigueSecurity teams should consider implementing processes to triage and validate breach claims efficiently. This includes leveraging threat intelligence feeds, monitoring for indicators of compromise (IoCs) and using threat hunting packages where available. By focusing on credible threats and filtering out noise from fake or unsubstantiated claims, security operations centers (SOCs) can reduce alert fatigue and allocate resources more effectively.
4. Communicate internally and externally with careIf your organization is named on a leak site but you find no evidence of compromise, communicate this clearly to stakeholders. Provide context about the prevalence of fake extortion claims and the steps taken to validate the threat. This helps prevent unnecessary panic and maintains trust with customers, partners and regulators.
5. Stay informed and collaborateContinue to monitor threat intelligence sources for updates on emerging actors and campaigns. Collaborate with industry peers and information sharing groups to stay ahead of evolving tactics, especially as threat actors increasingly use fake claims to sow confusion and disrupt operations.