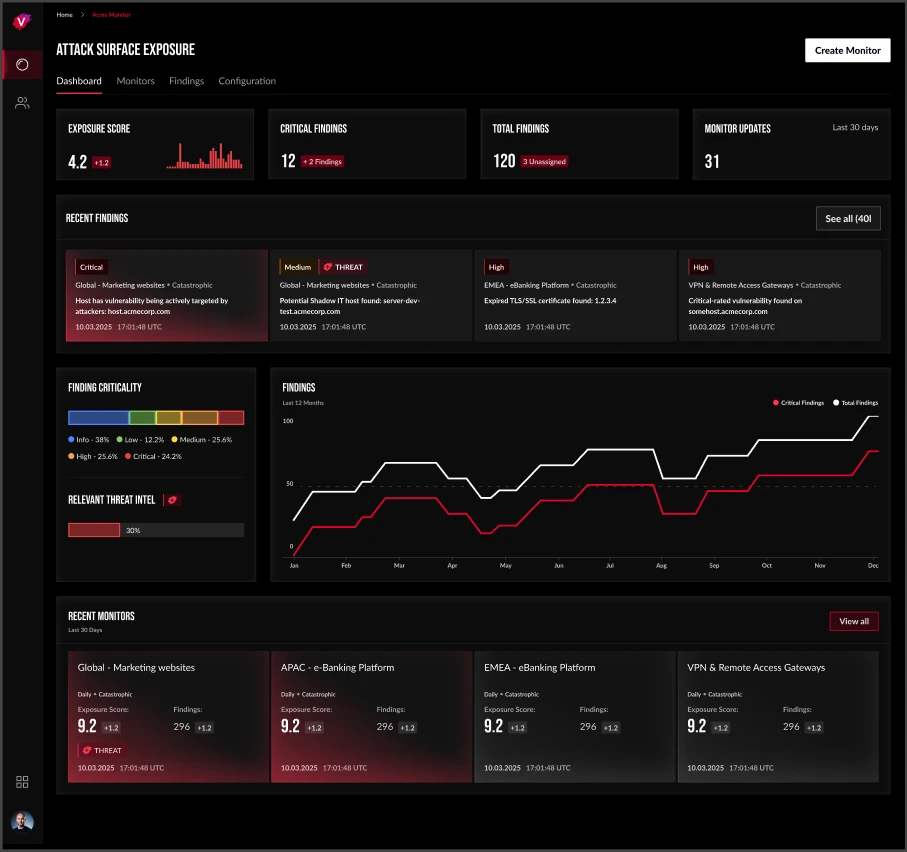
Know your attack surface better than adversaries do. Harness unmatched insights into digital threats to discover and prioritize high-risk vulnerabilities and exposures impacting your external attack surface

Intel 471’s Cyber Threat Exposure portfolio puts the power of CTI-driven security in the hands of all security and risk teams — even those that aren’t backed by mature CTI teams. Our Cyber Threat Exposure maps our unmatched insights into active threats and adversary activity with your attack surface exposures, helping your teams proactively mitigate threats and prioritize mitigation efforts.
Cyber Threat Exposure provides a growing number of CTI-driven modules optimized for your external attack surface management use cases. The Attack Surface Exposure Module empowers security and risk teams with CTI-driven attack surface management to discover and proactively mitigate high-risk exposures affecting your externally exposed digital assets. The Third-Party Exposure Module helps your team to independently monitor and mitigate your cyber risk exposure from third parties, such as suppliers, cutting out the guesswork that comes with relying on vendor security questionnaires. Cyber Threat Exposure’s use-case driven modules integrate select, high-quality OSINT data sources, and builds on the decade-long foundation of the underlying open source OSINT automation project.
To reap the benefits of digitalization and to mitigate risk, organizations need clear visibility of changes to their external attack surface and cyber risks from the security posture of third-parties such as suppliers and partners.
The Intel 471 Attack Surface Exposure module helps your security and risk teams quickly understand changes to your external attack surface with an asset risk-scoring dashboard to help prioritize patching. The Attack Surface Exposure module is a true CTI-driven external attack surface management (EASM) solution that maps active threats in near real-time to your external-facing assets using Intel 471’s unmatched insights into relevant threats, compromised credentials, information-stealer malware, third-party breaches, and actively exploited vulnerabilities.
The module gives your teams the CTI advantage, helping them to discover and remediate unknown, forgotten, and vulnerable assets before adversaries use them to gain entry and move laterally within your network. It helps your teams take control of ever-growing digital asset inventories across managed and unsanctioned “shadow” IT assets, web applications, software, and cloud resources. By correlating CTI data across the threat landscape, security teams gain early threat signals to proactively mitigate and prioritize the most at-risk exposures to reduce risk and improve security posture.
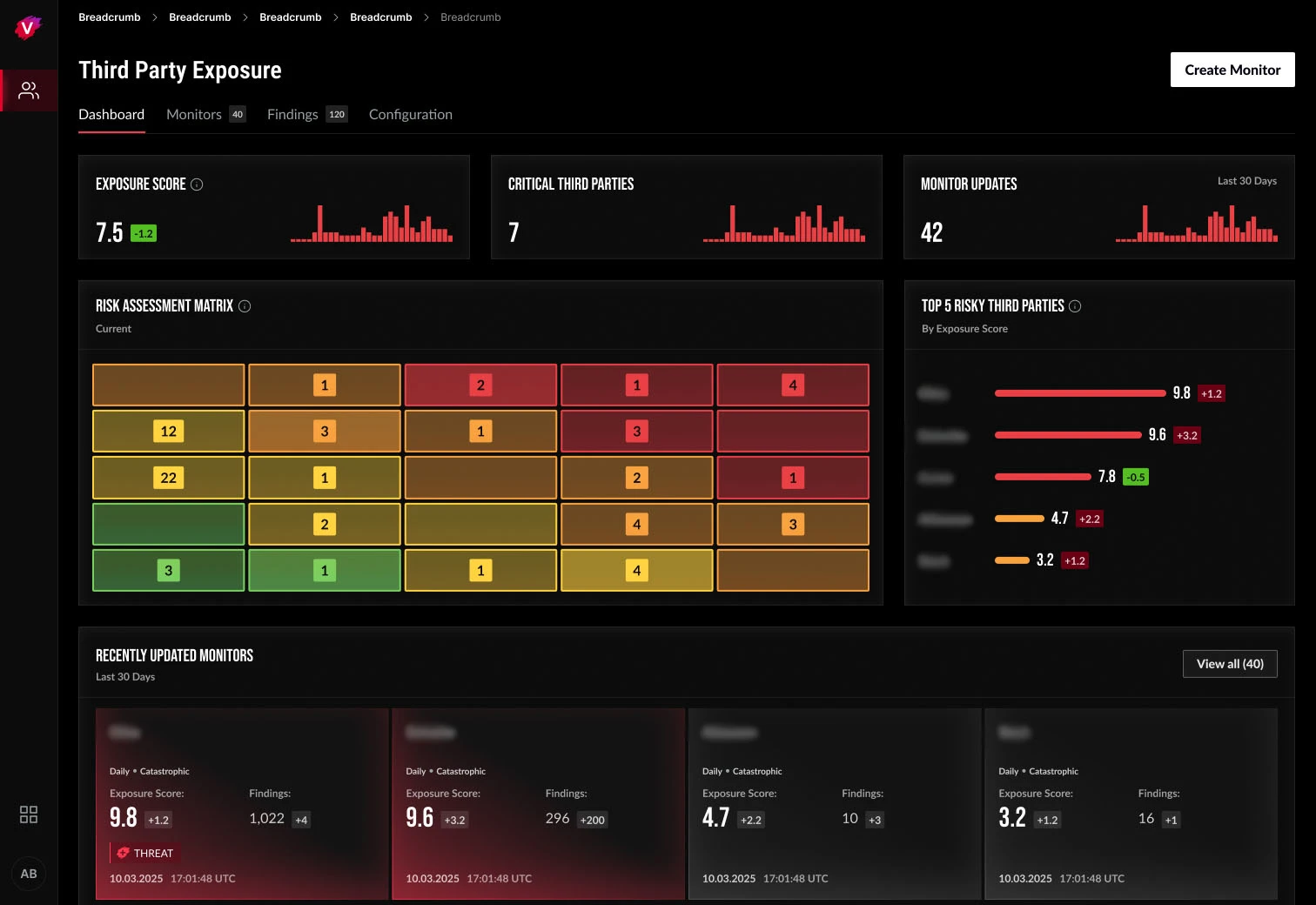
The Intel 471 Third-Party Exposure module gives security and risk teams the power to independently monitor and evaluate current and prospective key third parties, such as vendors. Cybersecurity regulations prioritizing digital supply chain risk management make our Third-Party Exposure module a must-have for security and risk teams in most sectors today.
The Third-Party Exposure module’s transparent risk-scoring dashboard guides cybersecurity and risk teams in managing third-party risks to their organization with continual visibility of third-party external attack surfaces. The Third-Party Exposure module makes it easy to monitor exposures and vulnerabilities affecting key suppliers’ external-facing digital assets. Users simply specify the vendors they want to monitor and target their domains, IP ranges or specific hosts of interest. The powerful module identifies a broad set of vulnerabilities and configuration issues with the flexibility to perform passive or active data collection on a daily, weekly or monthly basis. Built for quick decision making, the active interface helps teams easily monitor third-party cyber risk indicators, including critical CVEs, exposed databases, breach alerts and more affecting your third parties.
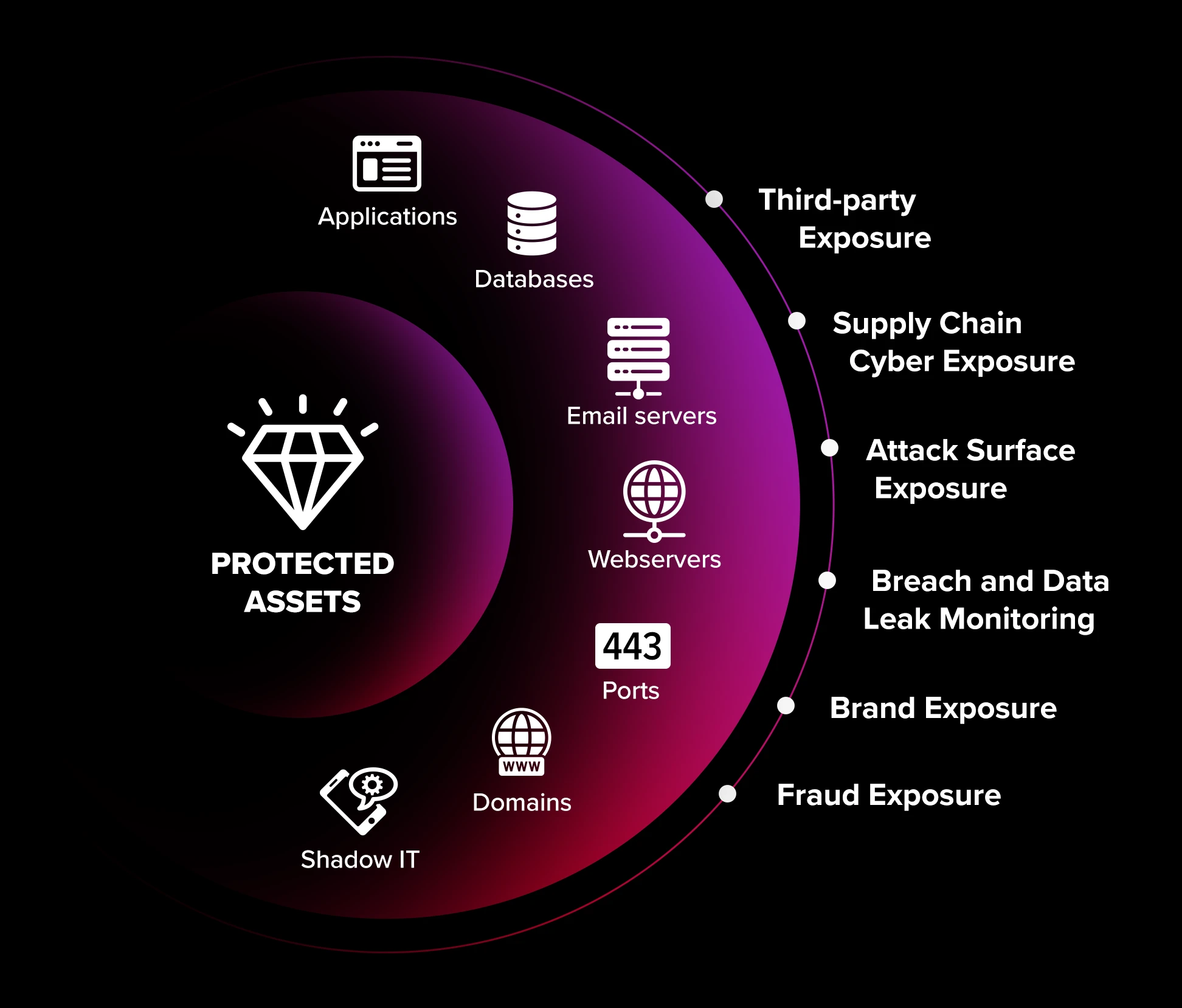
The Intel 471 Attack Surface Exposure and Third-Party Exposure modules are dedicated external attack surface management tools that harness Intel 471’s premier adversary intelligence to help security teams prevent attacks, reduce cyber threat exposure and achieve a significant return on investment. Don’t let your internet-facing assets or those of your third-party partners become an attacker’s foothold into your network.
Reduce the complexity of defending the dynamic attack surface by discovering, inventorying, and continuously monitoring known assets and new, unknown and unsanctioned internet-facing assets
Continuously monitor underground sources for actively exploited vulnerabilities, third-party breaches and compromised credentials using insightful, human-led and automation-assisted cyber threat intelligence (CTI)
Perform active testing for new CVEs, misconfigurations, outdated software, and malware connecting to your digital assets, and prioritize relevant, critical CVEs mentioned in underground forums
Know when CVEs on the attack surface are weaponized, as well as use a variety of high-quality OSINT sources to understand your attack surface visibility
Continuously monitor your attack surface, immediately see when assets are at a higher risk, and track threats to your brand and reputation
Improve regulatory compliance by independently performing passive, balanced or aggressive data collection on a daily, weekly or monthly basis
Integrate with other platforms or custom tools using the REST API
Identify, map and manage your external attack surface and reduce risk using cutting-edge threat intelligence.
Use Case
Don’t rely on vendor security questionnaires. Cut out the guesswork of managing third-party cyber risk with the Intel 471 Third Party Exposure module
Use Case
You can’t protect what you can’t see… Identify emerging threats to your attack surface in real-time. Our premier CTI positions you to see your organization as an attacker does and mitigate risks accordingly.
Use Case
Mitigate cyber supply chain risk, and monitor third parties for vulnerabilities with complete threat visibility and unparalleled, unique insights into attackers’ intents and motivations.
Use Case
Continuous visibility of data breaches and leaks contextualized with Intel 471’s deep cyber threat intelligence on malware, vulnerabilities, adversaries, and more to enable security teams to perform rapid remediation and prevention of future incidents.
Use Case
Protect your hard earned brand with our intelligence-driven brand protection solution. Quickly identify brand abuse in phishing campaigns, typosquatting domains, and social media impersonation accounts.
Use Case
Continuously track and analyze deceitful activities intended to steal or manipulate sensitive information for financial or personal gain. These activities can exploit vulnerabilities in systems or human behaviors, often targeting individuals and organizations alike.
WITH INTEL 471, YOU HAVE IT COVERED
The Intel 471 difference: Our Cyber Threat Exposure portfolio of solutions is driven by CTI experts who know the cyber underground and the cybercriminals who inhabit it like no one else. We know which exploits and vulnerabilities are being discussed, and which threat actors are most likely to leverage them. We monitor our sources continuously to deliver accurate and timely intelligence and alerts to your organization. Our threat intelligence capabilities, coupled with our understanding of the external attack surface, position you to look at your organization and your third parties as an attacker would, and mitigate those risks accordingly.
Stay informed with our weekly executive update, sending you the latest news and timely data on the threats, risks, and regulations affecting your organization.