Drive faster, more effective mitigation of cyber threats. Intel 471 delivers actionable insight into the tactics, techniques, and procedures used by your adversaries.

Gain unmatched visibility of cyber threats and the adversaries behind them with Intel 471’s award winning cyber threat intelligence (CTI). Use Intel 471’s Cyber Threat Intelligence portfolio to proactively protect your organization and strengthen decision making across strategic, operational and tactical levels. We identify who is targeting you, how and why. These insights empower you to act rapidly to mitigate emerging threats, track key trends across the cyber threat landscape to inform business strategy and anticipate and defend against adversaries that have your organization in their crosshairs.
Intel 471 delivers intelligence curated from a comprehensive spectrum of threat categories — including adversary behaviors, malware emulation, pre-exploit vulnerability insights, breaches, geopolitical events, marketplace and credential data. Our teams enrich this with expert insights and threat landscape analysis. Our platform then integrates our intelligence with rapid alerting, dashboards featuring interconnected data and finished intelligence products, to provide you the context you need to turn intelligence into action and defend against the threat of ransomware, exploit weaponization, credential abuse and more.
Gain a comprehensive understanding of your cyber threat landscape. Our CTI uncovers cyber threats across a wide range of categories:

Anticipate and out-maneuver cyberattacks by understanding what threat actors are planning and how they operate. Intel 471 provides timely insights into the methodologies of top-tier cybercriminals. We customize these results to your business, industry and geography, enabling you to make critical decisions based on trusted and relevant intelligence.

Mitigate the exposure of compromised credentials that could be used to impersonate users, gain unauthorized network access, steal data and commit fraud. Intel 471 provides constant monitoring and alerting of compromised credentials. We alert you to breaches involving your employees, VIPs, customers and third-party suppliers and vendors. We provide victim identity context and data to pinpoint how leaks occurred and whether the breach is new so your security team can begin remediation and investigations, fast.

Stay one step ahead of active and emerging malware threats. Using our sources, including our patented Malware Emulation and Tracking system (METS), Intel 471 enables real time insights into malware families, threats, adversaries, indicators of compromise (IOCs) and infrastructure updates. Tap Intel 471’s stream of technical indicators, campaign reporting and deep technical insights to harden your defenses against the latest threats.

Evolve your vulnerability management program by prioritizing your patch management. Intel 471 provides you with a lifecycle view of vulnerabilities, illuminating precursors to malicious activity. You gain ongoing monitoring and reporting of threats as they develop prioritized by risk and impact. Use these insights to understand emerging threats, prioritize patches and reduce your risks over time.

Disrupt adversaries committing fraud with your assets. With comprehensive monitoring of key marketplaces, Intel 471 provides early detection of when goods relevant to your organization, such as data and credit cards, are being sold or discussed. Your security teams can use this intelligence to act before adversaries can use them to their own advantage.
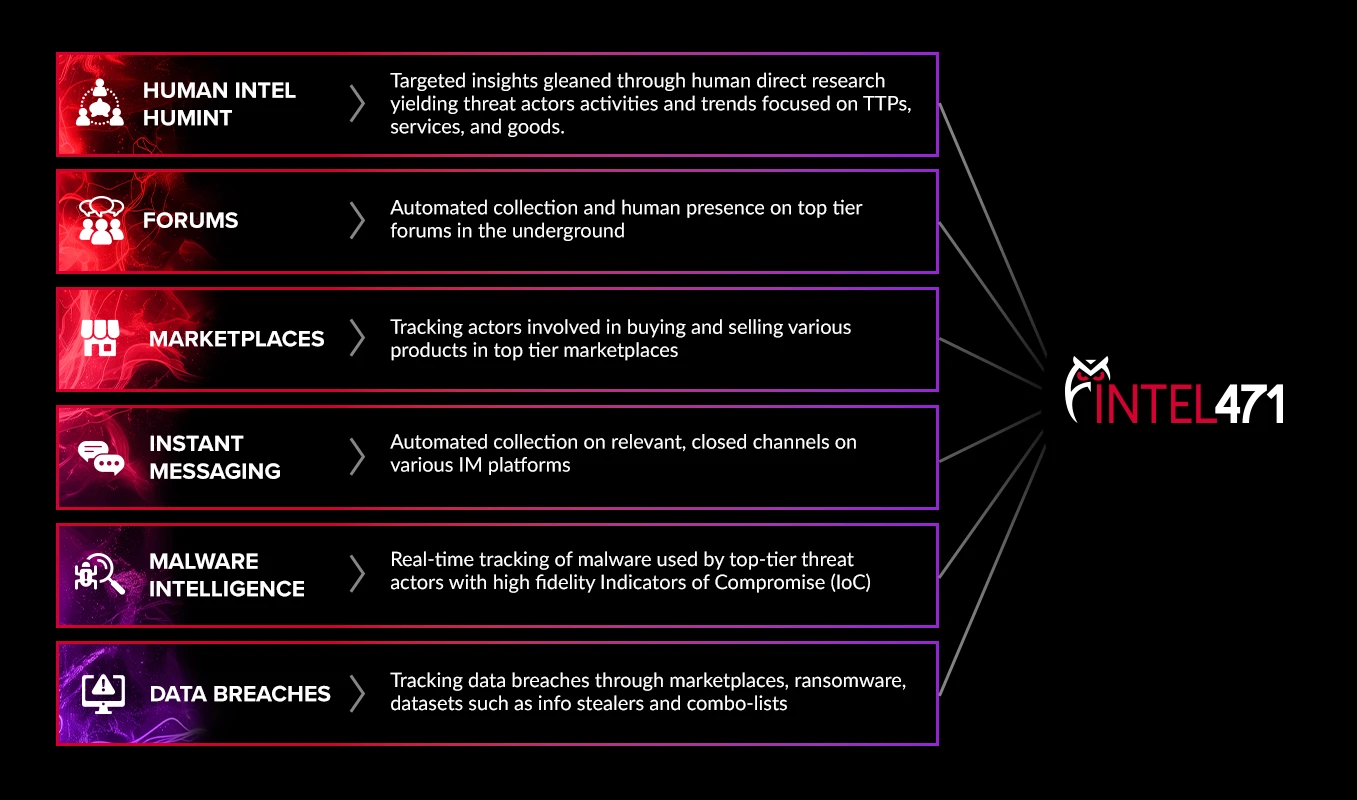
Intel 471’s CTI sources include covert sources, cybercrime forums, messaging platforms, marketplaces, malware tracking, infostealer logs, data breach logs, and more.
Continuous, automated data collection from the spaces where threat actors trade goods and discuss their operations – such as forums, marketplaces and infostealer logs.
METS provides ongoing surveillance of malware activity at the command-and-control level, delivering near real-time insights and deep context in support of numerous use-cases.
Direct engagement from cyber threat actors and sources within ‘closed’ spaces deep in the underground. Our research team uses cyber human intelligence (HUMINT) and follows ‘boots on the ground’ principles to gain credibility and forge relationships with threat actors. This unique access gives unrivalled insight into the methodologies of top-tier cybercriminals and early threat detection.
Intel 471’s curated CTI empowers every level of your organization. From indicators of compromise to strategic insights, our CTI mode helps you detect threats earlier, respond faster and prepare for emerging threats. Our core capabilities include:
Proactive Threat Monitoring: We uncover early warning signs of threats to your organization. Set up keyword and forum watchers to receive rapid alerts to threats identified across text, images and logos, so you can outpace them.
Awareness of Emerging Threats: Track emerging threats and trends across the cyber threat landscape. Whether the evolving associations between initial access brokers and ransomware gangs or significant geopolitical events and related hacktivist and nation-state campaigns, Intel 471 ensures you proactively harden your defenses.
Act on Intelligence: Explore how CTI connects with adjoining modes within the Verity 471 platform. Whether you identify a targeted exposure within your external attack surface in Exposure mode or deploy a pre-validated hunt package built off the behaviors unveiled by HUMINT to disrupt the undetected adversaries within your environment — we ensure our intelligence can be operationalized.
Enhance Incident Response: With operationalized intelligence, response teams can react faster and more efficiently to security incidents, minimizing potential damage.
Transform Vulnerability Management: Prioritize remediation based on precursors to exploitation in the wild, including proof-of-concept (POC) code, and the weaponization and productization of the code as it gets integrated into exploit kits.
Turbocharge Threat Hunting: CTI enables you to supercharge behavior-based threat hunts with deep intelligence regarding the tactics, techniques and procedures used by threat actors. Disrupt the cyber kill chain and defend your organization from undetected threats.
Invaluable Resources: Quickly evaluate evolving threats using dashboards for active malware campaigns, critical and weaponized vulnerabilities, credential statistics and information stealer log data and more. Deepen your understanding of the threat landscape with the ability to intuitively pivot between raw data and finished intelligence products. Focus on threats that matter using structured threat data to perform accurate searches for keywords, build queries and filter specific sources to fine-tune your results.
Measure Your CTI Team’s Success: Map your Prioritized Intelligence Requirements (PIRs) to Intel 471's Criminal Underground General Intelligence Requirements (CU-GIR) and the MITRE ATT&CK frameworks to ensure curated insights from the cyber underground are aligned with your strategic objectives.
Use our unparalleled CTI to satisfy specific use-cases within your organization, including:
Use Case
Deliver real-time, operationalized threat intelligence on active threats, vulnerabilities, and threat actors to enable faster detection, analysis and support for a well-prepared incident response investigation.
Use Case
Powerful vulnerability landscape monitoring allows you to leverage threat intelligence, and identify, assess and remediate cyber vulnerabilities to take control of your organization’s vulnerability risk.
Use Case
Continuous monitoring and alerting of compromised credentials, so you can accurately respond to, inform third parties about issues and defend against attacks stemming from accessed or stolen credentials.
Use Case
Discern how global events drive digital risk. Clear, concise and contextualized analysis of cyber threats stemming from geopolitical events so that security teams can strengthen enterprise risk management and refine strategic decision making.
Use Case
Vigilant monitoring by Intel 471’s dedicated team of cyber threat intelligence (CTI) experts across the globe helps your team stay ahead of ransomware threats and proactively hunt for ransomware behaviors inside your environment.
Use Case
Proactively detect malicious threats and stop cyber attacks with knowledge of attacker infrastructure and feeds of high-fidelity, technical indicators to identify attacks early.
Use Case
Protect your organization from Account Takeovers (ATOs). Intel 471’s targeted monitoring and unmatched visibility into the cyber underground helps organizations stay ahead of emerging ATO threats.
Use Case
Monitor extortion data leak sites and highly guarded underground marketplaces, forums and closed messaging groups. Take proactive mitigation steps with alerts for stolen cards, compromised credentials, third-party breaches and relevant vulnerabilities and support investigations with unique dark web insights.
Use Case
Track the most sophisticated and successful threat actors across the cyber underground and gain useful insights to proactively thwart cyber threats.
Use Case
Identify high-risk vulnerabilities through analyst driven analysis of real-world threat activity and continuous attack surface monitoring to enable effective, intelligence-driven patch prioritization.
Cut Through the Noise with Intel 471
Intel 471 delivers unique insights, curated cyber threat intelligence, and analyst-driven intelligence reports, bulletins, white papers, and threat briefs that provide you strategic and tactical insights into the threat landscape to ensure a proactive and comprehensive cyber security strategy. We cut through the noise and deliver you timely alerts, real-time intelligence, immediate threat visibility, and the intelligence you need to contextualize security threats. With structured data, less noise, and high-fidelity results, you can focus your team on what matters most to your organization, and rest assured that you are well positioned to harness actionable insight and are critically empowered.

“While many CTI vendors supplement their data with third-party intelligence and open-source information, Intel 471 distinguishes itself through its human intelligence-centered approach and timely reports. Leveraging a global team of analysts, Intel 471 extracts profound insights from threat actors and facilitates tailored research through RFIs, ensuring the relevance, timeliness, and uniqueness of its intel.”
-Martin Naydenov, senior industry analyst, Frost & Sullivan

Stay informed with our weekly executive update, sending you the latest news and timely data on the threats, risks, and regulations affecting your organization.