Rapidly expose compromised credentials and eliminate the risk they pose with real-time intelligence from rich sources.

Compromised credentials provide cybercriminals with initial access into your organization. Verizon's Data Breach Investigation Report 2025 indicates that credential abuse remains attackers’ preferred entry points, with 88% of attacks against basic web applications involving the use of stolen credentials. The chronic use of compromised credentials is unsurprising given the increasing digitization of business operations, users’ recycled passwords, and the high value placed on this data on the cyber underground. What’s more the rise of information stealing malware continues to lower the barrier of entry for attackers and flooding the cyber underground with compromised credentials for sale.
When the consequences of a credential-based attack harm both stakeholder trust and the bottom line, organizations must seek strategies for protecting their credentials against these attacks.
With intelligence fueled by a wealth of sources including underground marketplaces, third party breaches, infostealer logs, and direct engagement with sources, our CTI portfolio goes beyond early threat detection to present exclusive insights that contextualize the risk of credentials.
Understand if the compromised credential is part of a new leak or a repackaged set, as well as how and when the credential was stolen to take meaningful action against the risk presented.
Use our CTE portfolio to perform scans of your external facing attack surface to identify exposed and forgotten assets that cyber threat actors could use to test compromised credentials. Identify leaked credentials across open sources to compromised credentials of exposed assets putting your organization at risk.
Intel 471’s timely intelligence on compromised credentials gives you the depth and context required to identify illicit activity within compromised accounts before the damage is done. In our CTH portfolio, correlate CTI with pre-validated, behavioral hunts to identify the signs of credential abuse and derail undetected intrusions before they escalate.
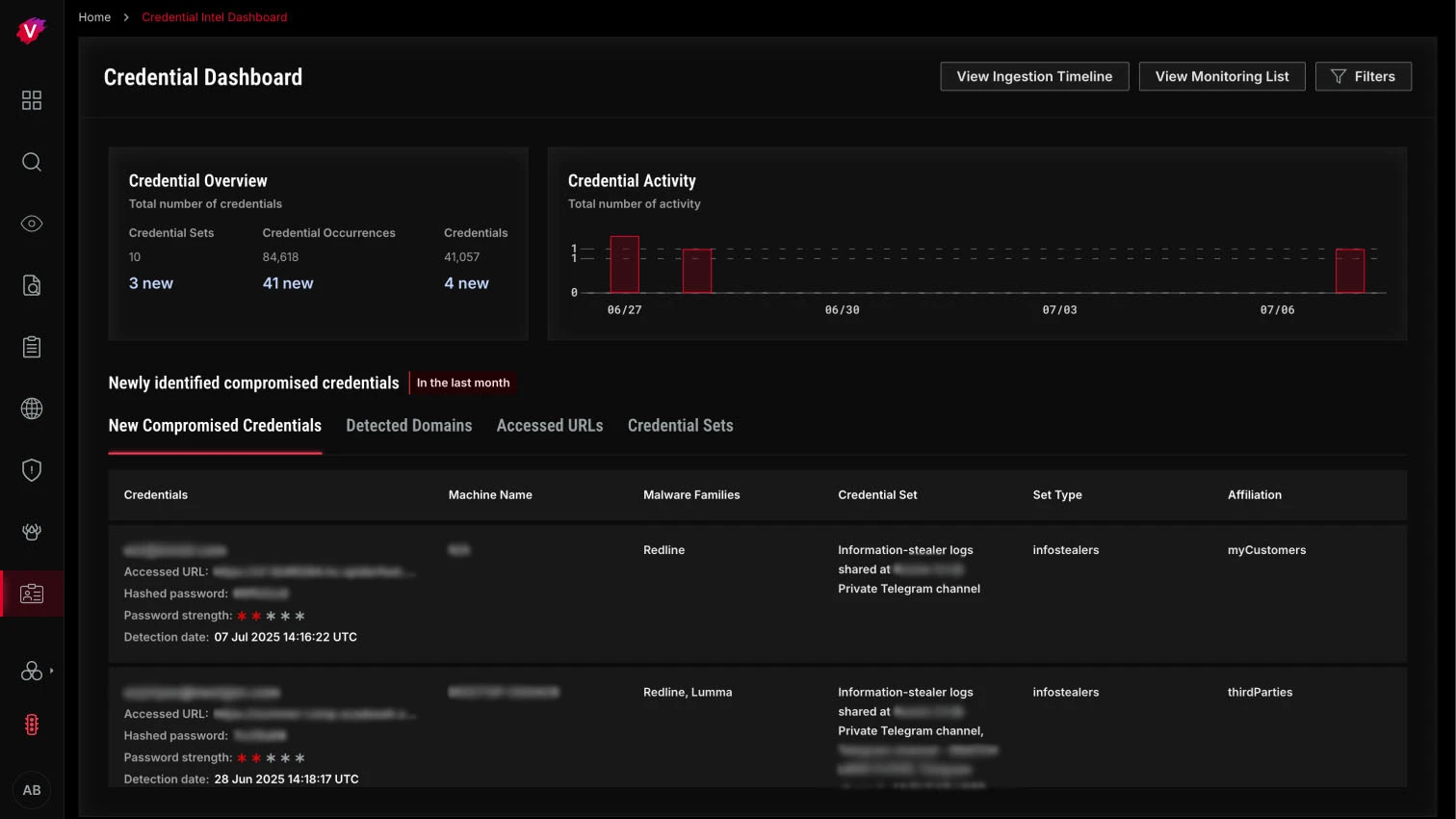
Delivered through our unified cyber intelligence platform, Intel 471 alerts you as soon as leaked credentials relevant to your stakeholders are identified. Identify unique credential sets and explore infostealer metadata to understand how and when a credential was stolen.
Intel 471 continuously collects data from tens of millions of data points – including marketplaces, covert human sources, and infostealer logs – to provide exclusive insight into your credentials, how they are being used and by whom.
We provide the context required to perform precise risk management. Explore infostealer metadata to better understand the source of the credential leak and discern a fresh breach and older data.
Take rapid action to remediate as Intel 471 alerts you on credential exposure across all your stakeholders – your employees, customers, VIPs, and third parties – as soon as they hit the marketplace. We give you the head start needed to prevent these being used for the attacker’s advantage.
Exposure mode not only identifies exposed assets on your external attack surface that attackers can use to test stolen credentials on to gain access, it also maps intelligence on compromised credentials directly to any exposures identified.
Once accounts are identified as compromised — whether through credential monitoring feeds or internal alerts — we can correlate that intelligence with endpoint behavior by analyzing activity originating from those users to help determine if the compromised account is being actively abused, particularly through post-exploitation behaviors.
Stay informed with our weekly executive update, sending you the latest news and timely data on the threats, risks, and regulations affecting your organization.